When you see some process with a weird name is running on your computer all the time, it’s not unusual to suspect of a malware infection. If this program resists on not describing itself, your suspicions can become stronger. Sure, using an up-to-date antivirus is a very good practice, but sometimes these processes aren’t as scary as their name sounds. Here are the innocent Windows processes, with sometimes with spooky names.
Control to Major Tom
You felt like your PC is kind of slowing down lately, and you are more than ready to blame it on to some pesky process that you find on your Task Manager. You nervously press Ctrl+Shift+Esc, and notice a peculiar exe is eating up resources. It reads Spaceman.exe and you don’t even know what is this process about. You ask, “Did you take your protein pills and put your helmet on?” absent-mindedly and with a calm manner.
Processes with the same name are mostly associated with some kind of partitioning tool. So, if you installed a program to manage your HDD space, there is no need to be alarmed. Even Windows itself describes it as a “storage space manager”. And you can also find it in the System32 directory.
But if you didn’t install a partitioning tool and you have this process active, you might want to have a malware check on your computer. Just to be on the safe side.
May I interrupt you for a moment?
System Interrupts is a process that you can find in Task Manager. It sounds like a process that follows any kind of error that occurs in the system and logs it or it handles the old “error report” or maybe the “windows is trying to find a solution” (which it never does!) windows.
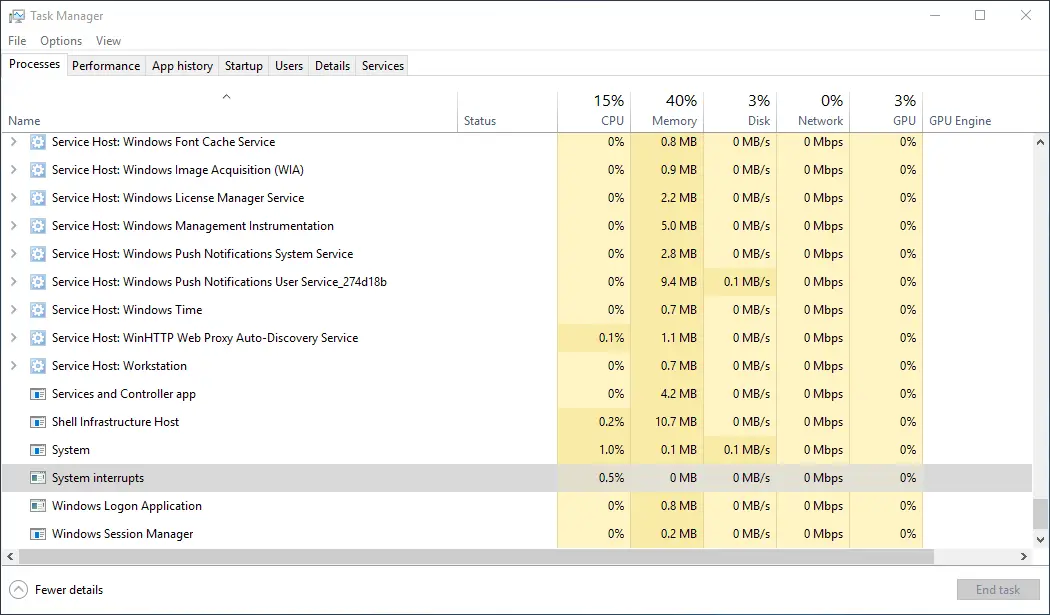
Actually, it is not even a “real” process. Normally, there are priority hierarchies between software and hardware processes on your PC. So, if a process with a higher priority starts while another process is running, you will see the value on System Interrupts rise. It actually shows the signals when the CPU gets interrupted from what it is initially doing. When the interruption is over, the values will go down. You might test this by yourself with just moving your mouse around or just typing stuff. Hardware activities have higher priorities than software activities.
Normally its value does not go too much over than 10% and if it does it’ll be for a brief period of time. But if you experience a high level of usage often, you may want to check your hardware.
The Vulkan, what?
Vulkan Run Time Libraries might make you very excited if you are a Star Trek fan. Thinking you have found something about the lore, and rushing to open it might give you a surprise though.

This is a cross-platform graphic API like OpenGL or DirectX. If you have an AMD or an Nvidia dedicated graphics card, you can be sure the driver update got this baby on your PC. You can find it in Apps and Features or Programs and Features.
It is a very new API and promises a lot of things like being simpler, less cumbersome for the system, more efficient. At least, these are what the developer claiming. Some modern games require this API or may just work better when Vulkan is active.
So if you are a gamer like me, you don’t want to uninstall this by accident. But if you are not, you could delete it I guess, but you can be sure that your next graphics driver update will install it back in.
Its own passport for your PC
In your Task Manager or maybe in the Services Panel you have found Microsoft Passport and wondered “Is my PC going anywhere without me? With all the precious data and web browsing history?” and started to wonder what is really going on.

This feature helps you to use your Microsoft Account more efficiently. You just need to sign into your account once per device and it does not ask you to do it again. And it does that through using a two-step verification process.
The process is done through Windows Hello. It may let you use your gestures for your second step authentication, respecting the device. The login method you choose is local to that device.
Windows provides this feature to make a more secure environment for users.


















